thick client testing toolkit part 2|Traffic Analysis For Thick Client Penetration Testing : services Learn how to use Wireshark, Burp Suite to analyze traffic for http protocol thick clients. Set up and configuration of Wireshark, Burp Suite, analyze traffic, and troubleshoot.
Nath Fischer (@nathfischer) no TikTok |540.8K curtidas.116K seguidores.pronta pra qualquer problema! hyperanhas original.Assista ao último vídeo de Nath Fischer (@nathfischer). Passar para o feed de conteúdo. TikTok. Carregar . Entrar.
{plog:ftitle_list}
Resultado da Eduardo Picasso,Edu Master,free videos, latest updates and direct chat. Language: Your location: USA Straight. Premium Join for FREE Login. Best Videos; Categories. Porn in your language; 3d; . Eduardo Picasso was most frequently tagged: gay (11), big-cock (9), new (7), sucking (6), big-ass (4), .
This repository serves as a guide for understanding and addressing these challenges, covering various aspects of thick client penetration testing such as information gathering, traffic . Welcome to Part 2 of the Thick Client Penetration Testing series! In this video, you'll dive deeper into the world of thick client security testing.
There are several different ways of performing a thick client pentest. The fun part is that the offense is almost always modular and you can choose which part to pick up first. Here’s a. Thick Client Pentesting Methodology and Checklist Part- 2 | by Ahmed Mehsania | Medium. Ahmed Mehsania. In this post, we’ll cover network testing in thick client applications and how it’s performed on different architectures. BetaFast is written with a three-tier architecture. Tier 1: The client displays and collects data. Tier 2: . Learn how to use Wireshark, Burp Suite to analyze traffic for http protocol thick clients. Set up and configuration of Wireshark, Burp Suite, analyze traffic, and troubleshoot.
thesinghsec/Thick
Traffic Analysis For Thick Client Penetration Testing
This blog post aims to delve into the world of thick client penetration testing, uncovering its significance, methodologies, and the tools employed to fortify these digital .
Introduction. (1:52) Installing tools. (4:11) Network connections with tcpview. (2:24) Network connections with Wireshark. (2:55) Exploring PE file with CFF Explorer. (1:04) File system .Learn practical thick client application penetration testing techniques. How to reverse engineer .NET binaries. Students will learn how to patch .NET binaries. How to identify and exploit .
Thick Client Pentesting Part
In the previous article, we have discussed the Lab setup of Thick Client: DVTAYou can simply take a walkthrough by visiting here: – Thick Client Pentest Lab Setup: DVTAIn this article, we are going to discuss how can we configure the DVTA application to connect to our server For this, I’m going to use one single window 10 instances for the entire setup. That . In this post, we’ll cover network testing in thick client applications and how it’s performed on different architectures. BetaFast is written with a three-tier architecture. Tier 1: The client displays and collects data. Tier . Launch CFF Explorer tool and load the DVTA file into it. DVTA is vulnerable thick client application. As you can see in the below figure, DVTA.exe will appear in the list of running processes. Introduction to Thick Client Penetration Testing – Part 1 July 29, 2017. Java Deserialization Exploit Resulting RCE on Thick Client Penetration Testing – Part 3 August 5, 2017. July 29, 2017. After getting the basics of thick client pentest, let’s delve into the very first steps you can take to commence thick client pentest.
Thick Client Pentesting Methodology and Checklist
As suggested by Ian, Burp Suite Invisible Proxy mode would be best for capturing request from Proxy unaware Thick client application. Consider an Thick client application making request to www.example.com. Inorder to capture . Thick clients can be referenced by many names: Fat Clients, Rich Clients or even Heavy Clients. Such applications follow a client-server architecture and can be developed using various programming . Welcome to Part 2 of the Thick Client Penetration Testing series! In this video, you'll dive deeper into the world of thick client security testing. Join me .Thick Client Application Penetration Testing Course Introduction Course Introduction (1:37) Help and Support . Part 1 (2:04) Lab Setup - Part 2 (18:44) The Pre-Course Challenge (2:32) Reversing + Configuring the server (10:48) Information Gathering Introduction (1:52) Installing tools (4:11) Network connections with tcpview (2:24) .

Here are the top tools used for thick client security testing: Burp SuiteWire Shark; Detect it Easy; Echo Mirage; CFF Explorer; Visual Code Grepper; DLL Hijack Auditor; 4. Manual Penetration Testing. Thick client penetration testing company provides complete manual penetration testing services based on business requirements and security . An application may gain access to sensitive information or system resources if it has unnecessary or overly permissive entitlements. For example, the com.apple.security.device.camera entitlement grants application permission to access the camera on a user’s Mac. However, starting from macOS 11 (Big Sur), this entitlement will trigger a .Burp Suite Enterprise Edition The enterprise-enabled dynamic web vulnerability scanner. Burp Suite Professional The world's #1 web penetration testing toolkit. Burp Suite Community Edition The best manual tools to start web security testing. Dastardly, from Burp Suite Free, lightweight web application security scanning for CI/CD. View all product editions
Thick Client Penetration Testing Tutorials - Part 2 ( Traffic Interception) Get link; Facebook; Twitter; Pinterest; Email; Other Apps - August 06, 2017 . Thick clients can be broken down into two types based on proxy settings: 1 1) Proxy aware. 2) Proxy unaware. Proxy aware are those applications which has settings in the application itself .A lot of the time they directly plug into a local or network adjacent database, therefore need a database connection string stored somewhere in the config. When i’m testing thick clients, never actually testing the code or app directly - always trying to bypass it and go for the database and make use of all the configuration files available.
Thick Client Penetration Testing: Hands
Detailed Traffic Analysis for Thick Client Penetration Testing – Part 2 July 29, 2017. July 29, 2017. Why thick client penetration testing? Thick client applications are not new having been in existence for a long time, however if given to perform a pentest on thick clients, it is not as simple as a Application Pentest. .
test case on white paper
Welcome again; I hope that you have read Part — 1🐱💻 of this Blog before coming here.. As we have already looked into the 3-tier application i.e. “BetaFast”. Now, it’s time to hack . 3. Using these credentials and a MySQL client (we used HeidiSQL), it was possible to access the MySQL server with full privileges. As an attacker we had the ability to alter or delete all user and .
In the previous article, we have discussed the reverse engineering of original DVTA application in the Lab setup of Thick Client: DVTA part 2In this part, we are going to systematically pentesting the DVTA application for various issues.Table of Content1. Prerequisites2. Information Gathering by using CFF Explorer3. Information Gathering by using Sysinternal Suite4. Information .
test scenarios for white paper
When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It provides functionalities like intercepting and modifying network traffic, performing code analysis, and executing exploits.Saved searches Use saved searches to filter your results more quickly GUI Testing. Like with Windows and Linux clients, the first step will be identifying the common user input surfaces and testing them for security vulnerabilities, such as SQL injection or cross-site scripting. . A Deep Dive into Penetration Testing of .
In part1 I talked about some of Burp's functionalities with regards to testing non-webapps. I did not expect it to be that long, originally I had intended to just shared some quick tips that I use. Now you are forced to read my drivel. In this part I will talk about Target > Scope, Proxy > HTTP History and Intruder/Scanner. I will discuss a bit of Scanner, Repeater and .
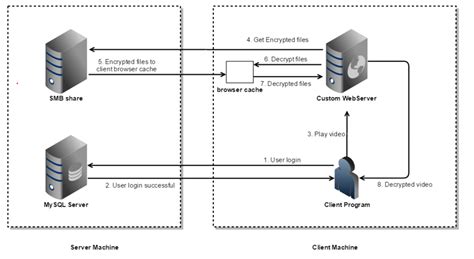
Hi👋🏻 Cyber Security people; I hope you guys are doing well.I am back with another Blog which again focuses on — “Thick Client Security Testing”.As I’ve already published a blog on .Simple automated scanning is not sufficient and testing thick client applications requires a lot of patience and a methodical approach. . Thick Client penetration testing is an integral part of your overall application security strategy, more particularly for mission-critical apps, as it helps you identify & fix vulnerabilities to ensure your . In the rapidly evolving landscape of cybersecurity, organizations face an increasing challenge to secure their software applications and protect sensitive data. Among the arsenal of defense mechanisms, penetration testing, or "pen testing," has emerged as a vital practice to identify and mitigate vulnerabilities. In this article, we delve into the fascinating world of thick . Desktop Client → Application Server → Database
Diagram 1.2 (3) the thick client can be divided into two parts as shown below: (3.1) exe files or (3.2) web-based launcher like a java-based application.
testing interview questions white paper
testing interview questions why the paper is white
webFor this dino, there are 2 methods (Honest). Here they are: METHOD 1: The Trap. The usual. 2x2 stone trap (4 stone floors, 16 stone walls and 4-6 ramps), cost efficient and simple. Lead the spino into the trap and tranq it down. When taming, make sure to watch its torpor as it drains quite fast! METHOD 2: Trapless.
thick client testing toolkit part 2|Traffic Analysis For Thick Client Penetration Testing